Accounting Auditing. From Social Security benefits to banking a lot of our personal and financial information has gone online.
The number of people affected by identity theft grew by 500000 people from 126 million in 2012 to 131 in 2013 with escalating losses as well.

. Online Mobile 6 CPE Credits. There are several obstacles that make the investigation of identity theft cases and the likelihood of arrests difficult US. Topics within identity theft training programs include.
Three stages of identity theft have been identified. Vodafone has launched an investigation after a cybercrime group claimed to have stolen hundreds of gigabytes of source code from the telecoms giant. Advanced Fraud Techniques.
A useful definitional model of identity theft has been proposed by Sproule and Archer9 Identity theft encompasses the collection of personal information and the development of false identities. Identity Theft Investigation More than 5000 000 people nationwide will become identity theft victims in the year 2000 an increase of more than 450 000 annual cases over the last 5 years. For example training in identity theft usually involves providing investigators with the newest investigative techniques resources and victim-related issues.
Identity theft has swiftly become a serious issue for victims police and prosecutors and is a problem that is requiring an increased commitment of resources by private enterprise. Online organisations commonly use electronic commerce approaches. If an identity theft suspect has been arrested request copies of the mug shot fingerprints palm prints if taken and the booking or arrest sheet.
If you have been a victim of Identity Theft take the following steps immediately. For example identity theft cases can be highly complex or the offender may have committed the theft in a different jurisdiction from where the victim resides making it difficult to secure an arrest warrant. This course will discuss at minimum legal techniques for darknet investigations including identity theft money laundering access device fraud and conspiracy charges utilizing narcotics case.
Identity fraud refers to the use of a false identity to commit fraud. Emphasis is placed on victim issues and providing resources for investigators to utilize in identity theft cases. Identity theft occurs when someone uses your identity in a crime or fraudulent act.
As you may be aware the FBI prioritized and restructured its approach to cyber crime in its many forms a little more than two years ago with the establishment of the Cyber Division. Fraud affects more than organizations. Go to IdentityTheftgov or call 1-877-438-4338.
Accordingly targeting Identity Theft and related cyber crime activity will remain a priority of the FBI. However these have some limitations in the m-commerce. Do we possess the right tools to adequately prevent.
The FBI is seeking victims whose personally identifiable information PII may have been misused between September 2018. You may choose to file a report with your local police department. PInow put together an infographic highlighting ID theft in America.
This course will define and demonstrate access to the darknet for the purposes of identifying and tracing narcotics distribution. 2 days agoVodafone Investigating Source Code Theft Claims. Identity theft and the Internet have brought fraud right into our homes and can affect every part of our lives.
The hacker group calling itself Lapsus claims to have obtained roughly 200 Gb of source code files allegedly representing approximately. Include as many details as possible. To schedule a training session please contact Scott Morrill at 801-281-1218.
Legal issues involving identity theft. E xamining identity theft suspects requires systematic methodical techniques designed to yield evidence for possible prosecution. Report identity theft to the FTC.
The ID Theft investigation framework disti nguishes the examination in the victims and the. Contact the card issuer-Report the fraud immediately by phone and in writing-Close all of the affected accounts. Call the Fraud Departments of the three major credit bureaus.
The University of Glamorgan and is currently working towards a PhD in Data. Fraudsters side and the first level of this investigati on process analysis was hence presented. Global identity theft protection services market was valued at US 515696 million in 2022 and is expected to reach US 852207 million by.
What if I am being notified about identity theft reports but there are no new reports on my Reporting screen in FATPOT. Online ID theft techniques investigation and response 77. Seeking Victims in Identity Theft Investigation.
This paper presents an evaluation of the approaches used in identity theft prevention and suggests guidelines to overcome the weaknesses in m-commerce. Several important premises were acknowledged as the. It can happen to anyonebut there are steps you can take to protect yourself and to recover if it happens to you.
Created and managed MVPAL boxing program and revised School Criteria Incident. Fraud and Identity Theft Investigative Techniques Community Relations Law Enforcement Crime Trend Analysis Strategic Planning Accomplishments Uncovered money laundering and counterfeiting ring during routine car stop by leveraging investigative techniques and methods. The Major Cities Chiefs Association MCCA recognized the severity of this problem in 2003 and surveyed its members to explore police-related identity theft issues.
Mining of Intrusion Detection Systems. CIPPIC Working Paper No2 Techniques of Identity Theft 1. INTRODUCTION In order to prevent detect and deal with the aftermath of identity theft it helps to have an understanding of how it happens in the first place.
Based on the information you enter IdentityTheftgov will create your Identity Theft Report and personal recovery plan. The threat of identity theft is on the rise. As technology advances so do the techniques used by identity thieves.
The state with the highest per capita rate of reported identity theft complaints was Florida followed by Georgia and California. This training course is designed to provide an overview of identity theft and trends as well as a look at investigation techniques in identity theft cases and crimes. Identity theft since it may occur only once and be discovered quickly by the credit card issuing company often before even the individual card holder knows it.
Other types of identity theft such as account takeover are more involved and take a longer time to complete. How does my agency request training on IRIS the FATPOT PortalOne software and Identity Theft investigation techniques.

Cyber Crime Investigation Making A Safer Internet Space

Identity Theft Investigations Pinow Com

Pdf Online Id Theft Techniques Investigation And Response
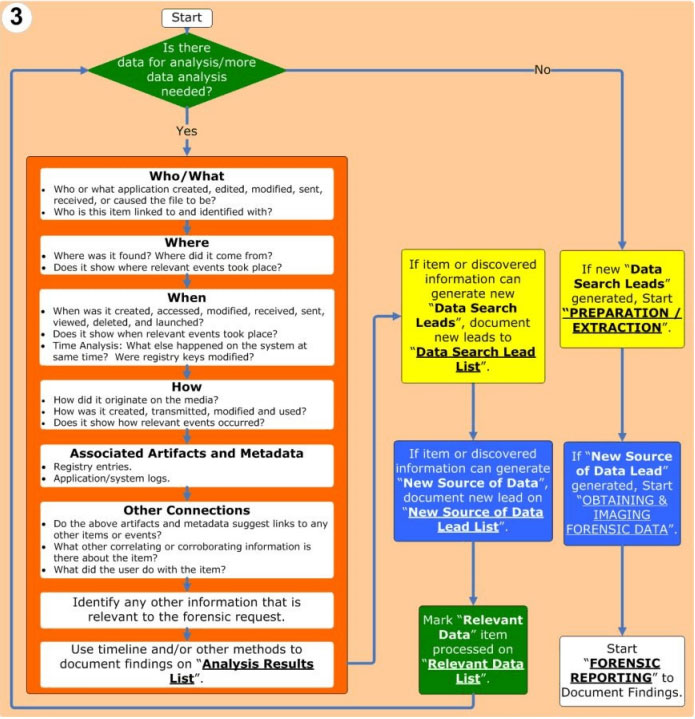
Computer Forensics Digital Forensic Analysis Methodology

Tips And Advice To Prevent Identity Theft Happening To You Europol


0 comments
Post a Comment